Network-Wide DNS Blocking of Advertising, Telemetry, and Malicious Domains using Pi-hole and OPNsense
Table of Contents
In my home network I wanted to set up a dedicated Pi-hole installation so that I could have network-wide ad blocking. Additionally, I could reduce the telemetry/tracking performed by applications and operating systems as well as potentially block malware. Pi-hole provides the ability to view the DNS traffic on my network on a per device basis, which may present valuable insight in detecting unusual activity on the network.
While OPNsense can be configured to provide DNS blocking, I really like the graphs and logging of Pi-hole. I can quickly view the DNS traffic and see if there are any spikes in the data as well as see a list of top allowed and top blocked domains. This is useful in determining if certain domains should be whitelisted or blacklisted.
Once I had Pi-hole up and running on my Raspberry Pi (affiliate link) , I had to determine how to properly configure my OPNsense router. The Pi-hole documentation states three ways to configure your network. There is technically a fourth option if your router does not support configuring DNS settings. Since we are using OPNsense, we can rule out option #4 immediately since it allows for DNS modifications:
- Define the Pi-hole IP address as the only DNS entry in the router DHCP settings
- Advertise the Pi-hole IP address via dnsmasq in the router (if your router supports such an option)
- Manually configure each device to use the Pi-hole IP address as the DNS server
- Use the Pi-hole DHCP server rather than your router’s DHCP server
For my purposes, option #3 is off the table because I do not want to manually configure the DNS of all of my devices, and I want to prevent users or devices from changing their DNS settings. When I first set up OPNsense and began creating my firewall rules, I configured my firewall to block any DNS servers that are not assigned by my router to prevent manually configured DNS settings on network devices. If users or devices are allowed to set their own DNS settings, DNS requests could be made to other internal or external DNS servers and would therefore bypass any Pi-hole or other DNS filtering. That would defeat the purpose of installing Pi-hole on the network!
That leaves me with option #1 and #2. I do not like option #1 because it will look like all of my DNS traffic is coming from my router instead of my individual devices. The instructions on Pi-hole states you can fix that by editing the /etc/hosts file on the Pi-hole server, but that is extra work since you have to enter IP address and hostnames for every device on your network. Also, you will have to give all of your devices a static IP address. Otherwise, the statistics will inaccurately track devices when IP addresses change or it will only display the router IP address if you have not yet mapped an unknown IP address.
So option #2 it is! The benefit of option #2 is that we only need to configure the OPNsense and Pi-hole settings in order to have per device DNS statistics for your entire network. This requires less maintenance and any new device that joins the network will automatically be subjected to the Pi-hole DNS filtering.
But how should you configure the OPNsense router and Pi-hole settings? There are two ways you could go about doing this.
First way

Second way
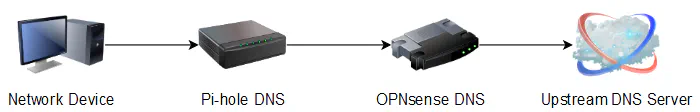
Both ways will work to provide DNS blocking by Pi-hole. With the first way, OPNsense would advertise your Pi-hole as the only DNS server to your network devices via the DHCP settings or static mapping settings. All of your devices would then use the Pi-hole for their DNS resolution and the Pi-hole would then forward non-blocked DNS requests upstream to the external DNS servers you selected when you installed Pi-hole such as the default Google DNS.
However, the second way makes use of DNS chaining by adding an extra hop so that local network hostnames will resolve correctly. This is helpful if you run any servers on your home network and you like accessing them by their hostnames instead of their IP addresses. As with the first way, OPNsense would advertise the Pi-hole as the only DNS server to network devices, but the difference is that the upstream DNS server for the Pi-hole is set to your router’s IP address as the only upstream DNS server. This allows the OPNsense unbound DNS resolver to provide local hostname resolution. OPNsense then forwards any non-local DNS requests to the external upstream DNS servers you have configured in OPNsense.
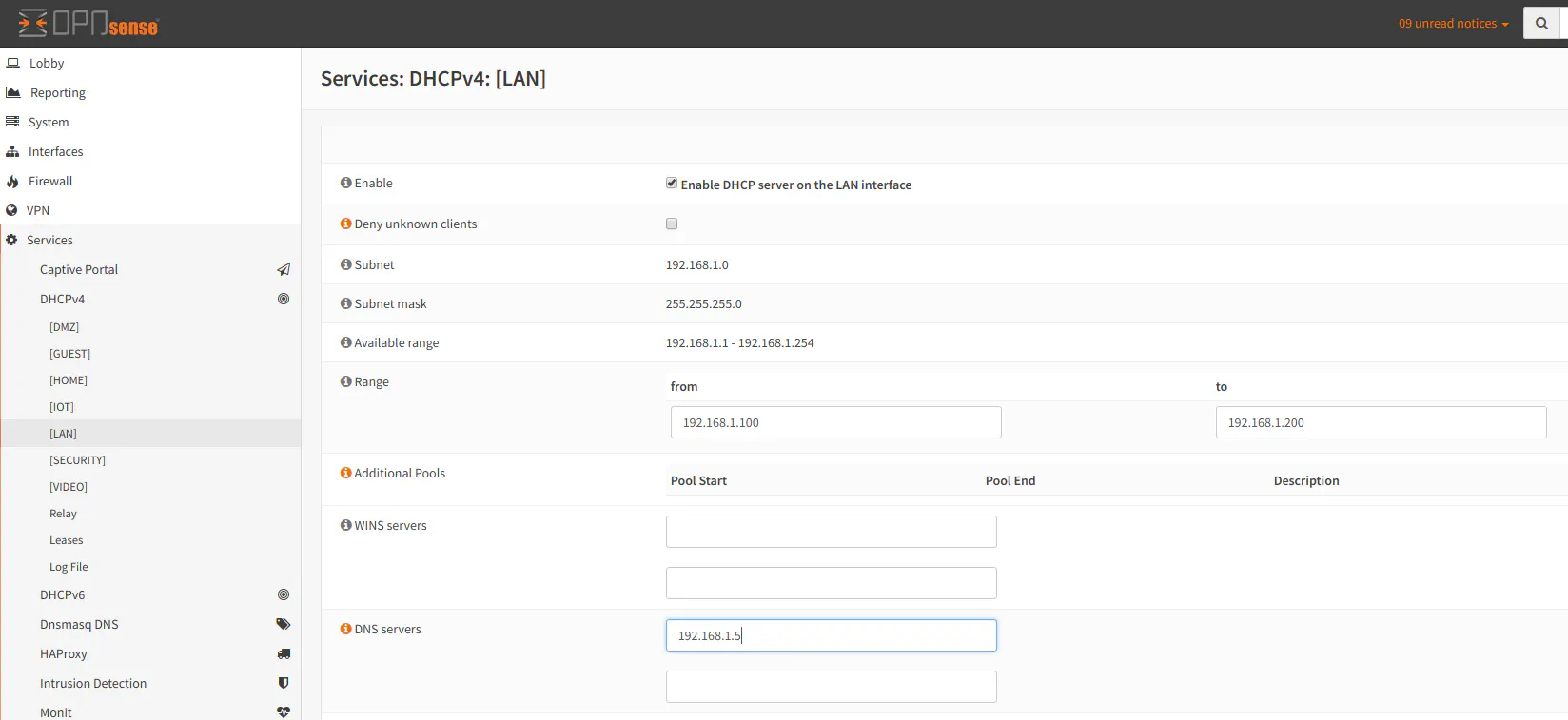
To configure the DNS for the second way, you will need to configure the DNS servers in OPNsense for your LAN interface and any other interface/VLAN networks so that your network devices receive the DNS server information for the Pi-hole server:
Configure the upstream DNS servers of your choice in OPNsense in the Administration -> Settings -> General page. It should point to your external DNS servers such as OpenDNS:
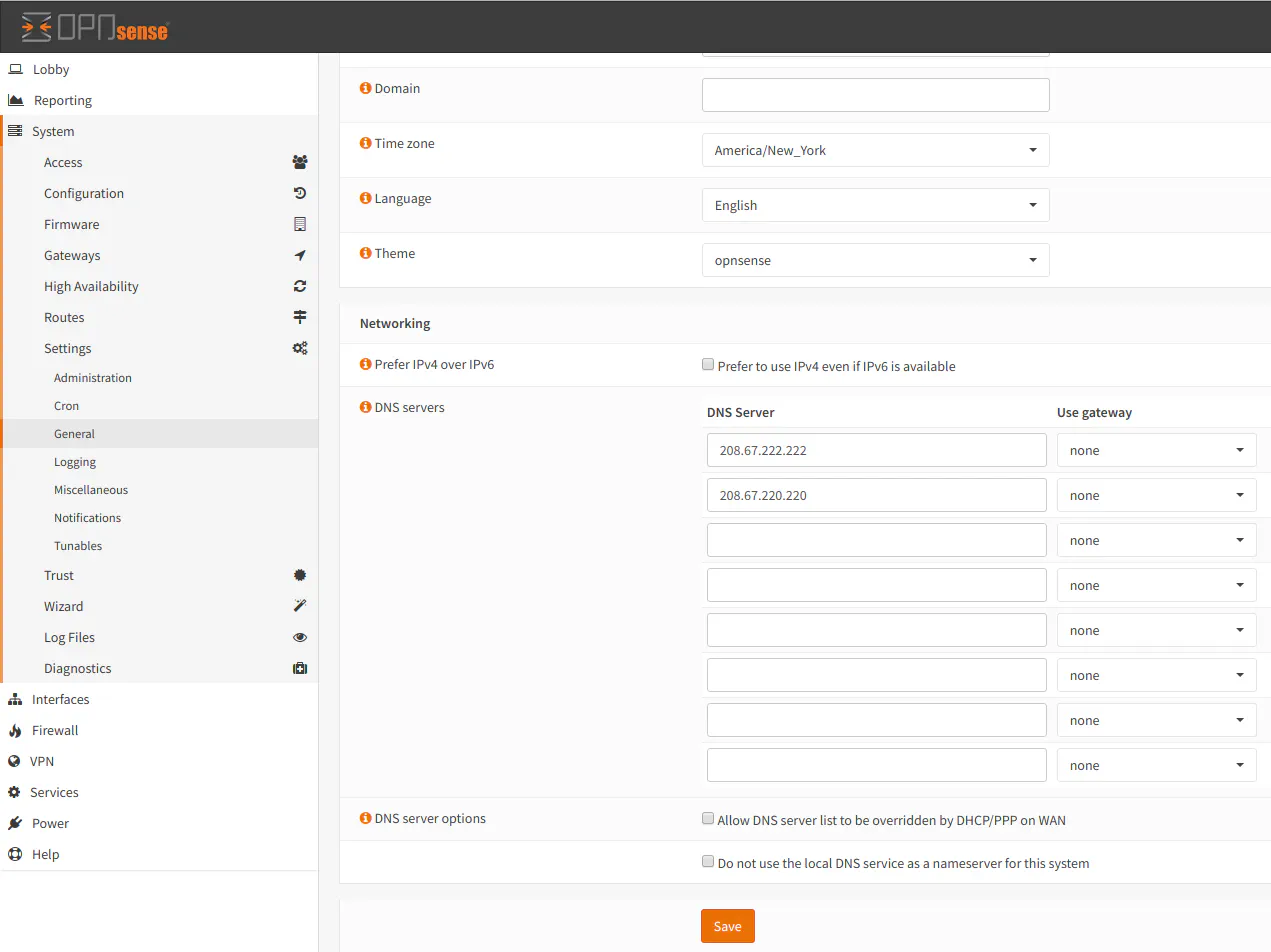
Note: If you plan to use your ISP DNS servers, you may leave the main DNS servers blank and the DNS servers will be set via DHCP from the ISP. Be sure to check the box “Allow DNS server list to be overridden by DHCP/PPP on WAN” to allow the DNS of the ISP to be set via DHCP.
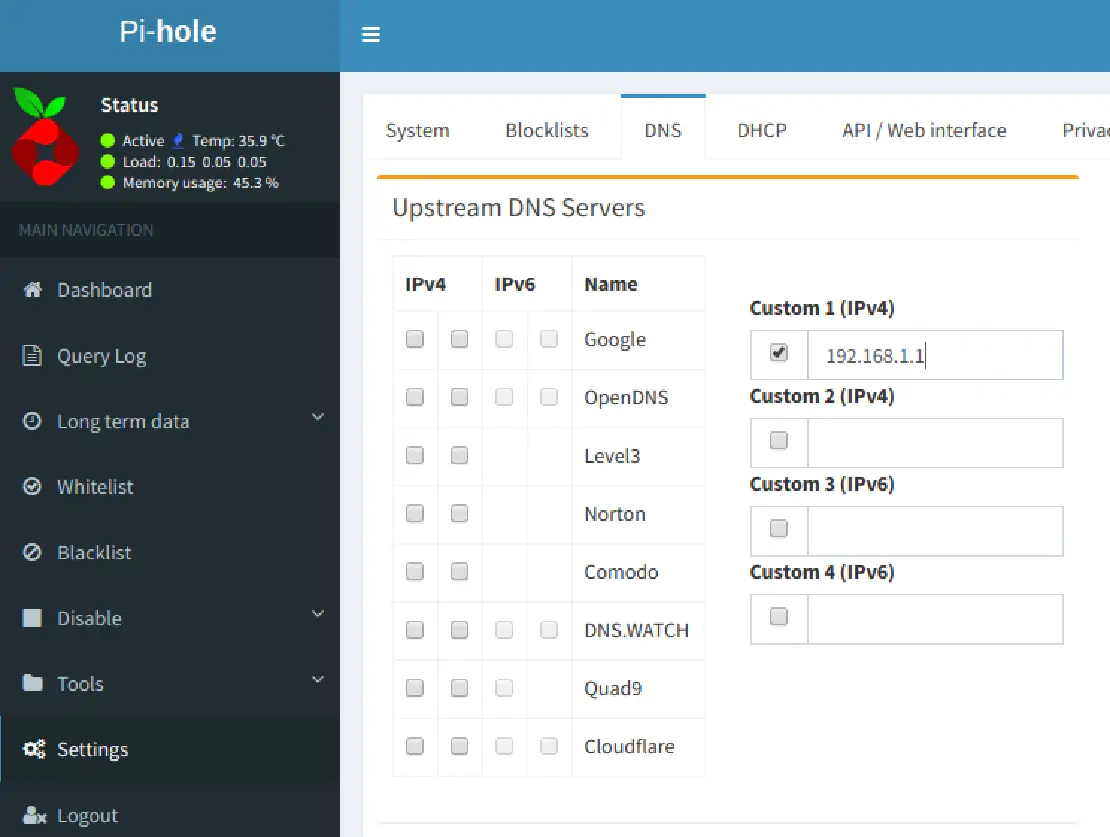
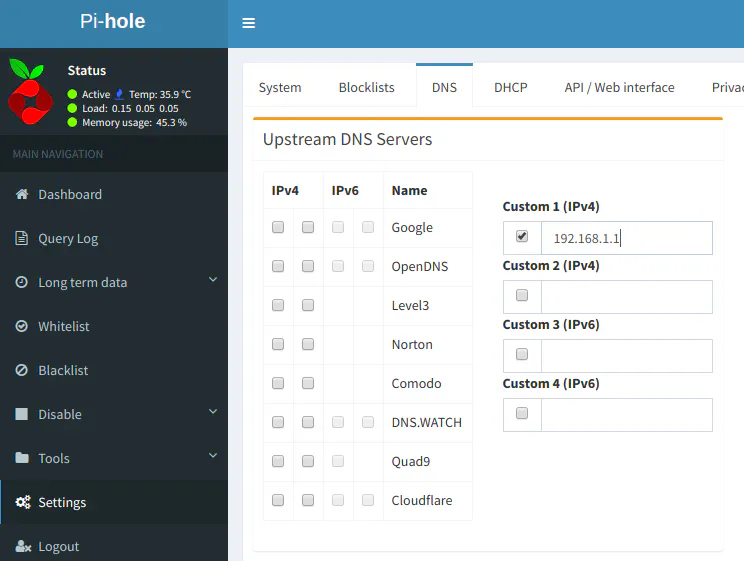
In the Pi-hole Settings > DNS page, you will need to change the upstream DNS servers by unchecking any of the boxes for the DNS providers under IPv4 and IPv6 and provide your router IP address as the only IP address in the Custom 1 (IPv4) box. This will make Pi-hole forward all upstream requests to your router.
If you are using VLANs, you will also need to adjust the firewall rules to allow your devices to communicate with your Pi-hole server. Visit How to Use Pi-hole DNS with VLANs for more information.
That’s it! You only need to change the DNS settings in OPNsense and Pi-hole. You will know that you have configured everything properly if you see your router as the main IP address/hostname that DNS requests get forwarded to. All DNS requests should be either blocked (aka “pi-holed”), forwarded from Pi-hole’s DNS cache, or forwarded to your router IP address.