How to Configure DNS over TLS (DoT) Using Unbound DNS in OPNsense
Photo by jarmoluk from Pixabay
Table of Contents
Previously, I wrote about how to configure DNS over HTTPS using DNSCrypt-Proxy. Since Unbound DNS in OPNsense does not support DNS over HTTPS (DoH) directly, it was necessary to use the DNSCrypt-Proxy plugin. The plugin also supports DNS over TLS (DoT). However, I discovered while browsing Reddit that Unbound gained native support for DoT at some point in time, which is very nice. Because of built-in support for DoT, the configuration of DNS over TLS becomes pretty trivial.
For the uninitiated, DNS over TLS is another way to encrypt DNS requests. Some of the differences between DoT and DoH are that DoT uses UDP and port 853 while DoH uses TCP and port 443. DNS requests sent via DoH will blend in with other HTTPS traffic while DNS over DoT will be more noticeable on port 853. Both methods should provide similar levels of security. However, the DoH option may provide some increase in privacy. For those who want to monitor their networks, DoT may be a better option since that traffic is separate from all of the other HTTPS web traffic.
Add the DoT Servers to Unbound
To configure DNS over TLS, go to the “Services > Unbound DNS > DNS over TLS” page. You will see the empty page the first time you visit it. Click on the “+” button to add a new DNS over TLS server. I am going to use Cloudflare’s DNS servers as an example, but it should work with any DoT server.
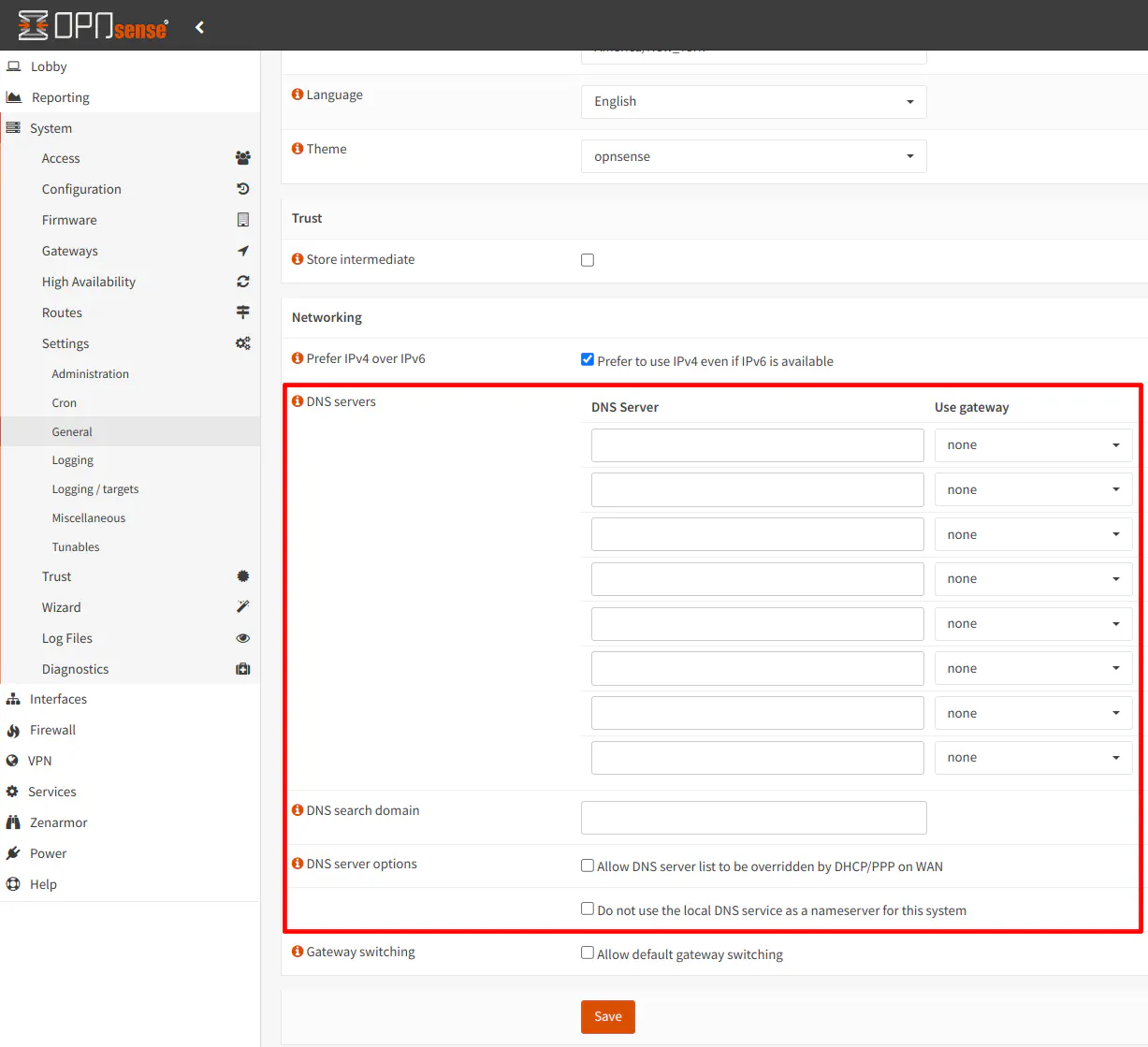
You will notice on the “DNS over TLS” page an option for “Use System Nameservers”. That option can be left unchecked to ensure the DNS servers configured on DNS over TLS are used. Note that you do not need to enter any DNS servers on the “System > Settings > General” page if you are using DNS over TLS.
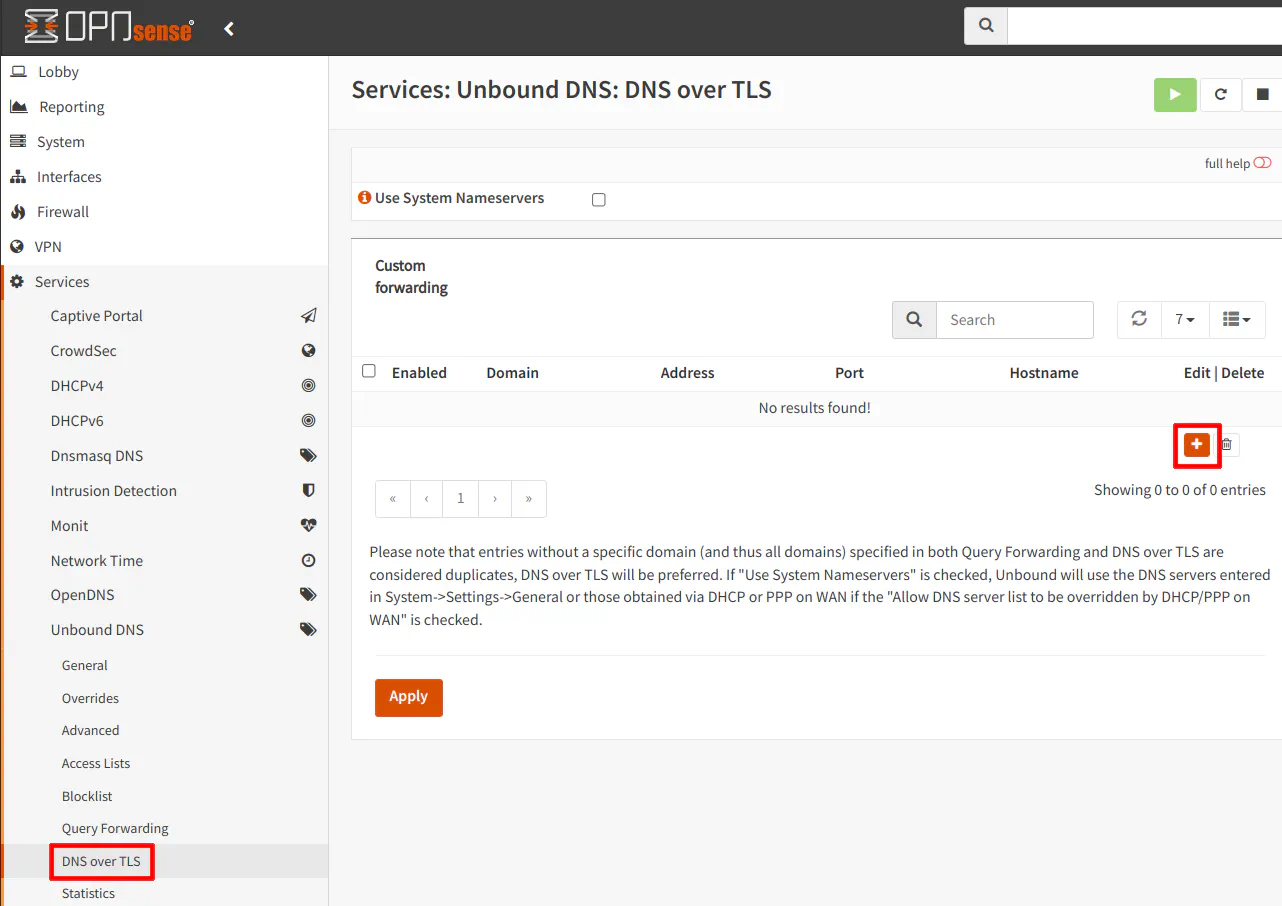
You may leave the “Domain” box empty unless you want queries for a specific domain to use a different DNS server. There may be scenarios where this would be helpful, but if you leave it blank, all DNS queries will use the specified DNS server. Enter the 1.1.1.1 for the “Server IP” and 853 for the “Sever Port”. The “Verify CN” option is not required by highly recommended to validate the Common Name on the DoT server’s certificate. It helps to improve security by ensuring you are connecting to the desired server and not some “man in the middle” server. For the 1.1.1.1 server, the CN is cloudflare-dns.com. I found the proper values for the “Verify CN” option on an OPNsense forum post.
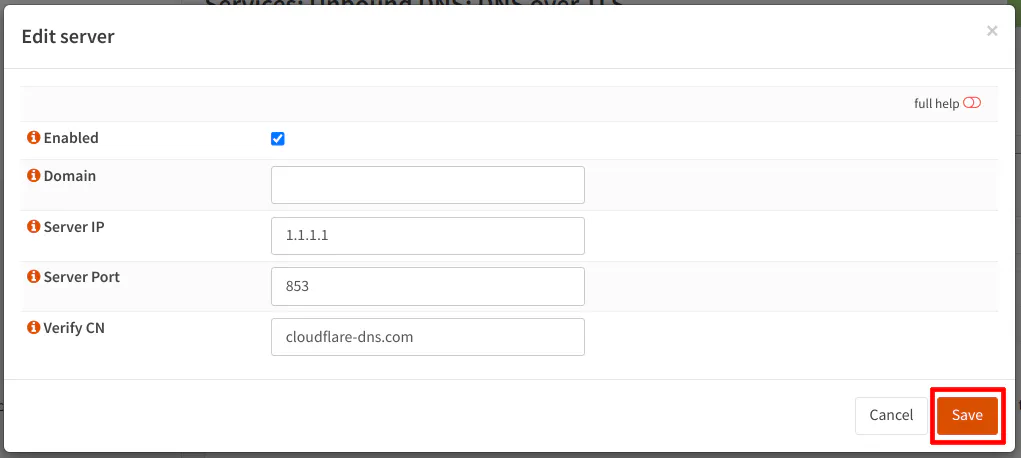
After clicking “Save”, you will notice the server appear in the list. You need to click the “Apply” button for the changes to take effect.
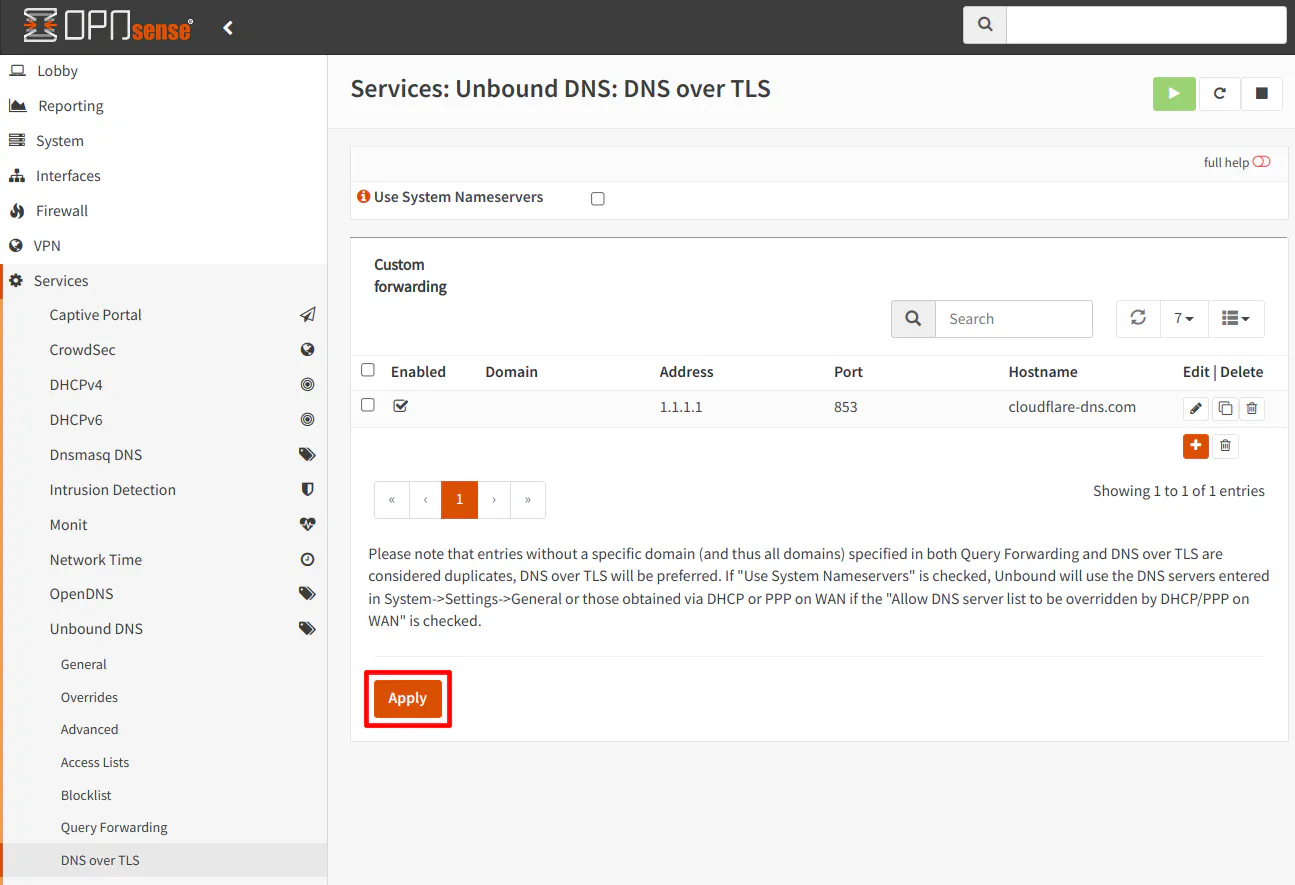
Before applying the changes, you should add the secondary 1.0.0.1 DNS address as well as add the IPv6 DNS server addresses (2606:4700:4700::1111 and 2606:4700:4700::1001) if you are using IPv6 on your network. You can see below what a minimally complete least should look like since you should specify a secondary server for both IPv4 and IPv6 DNS servers.
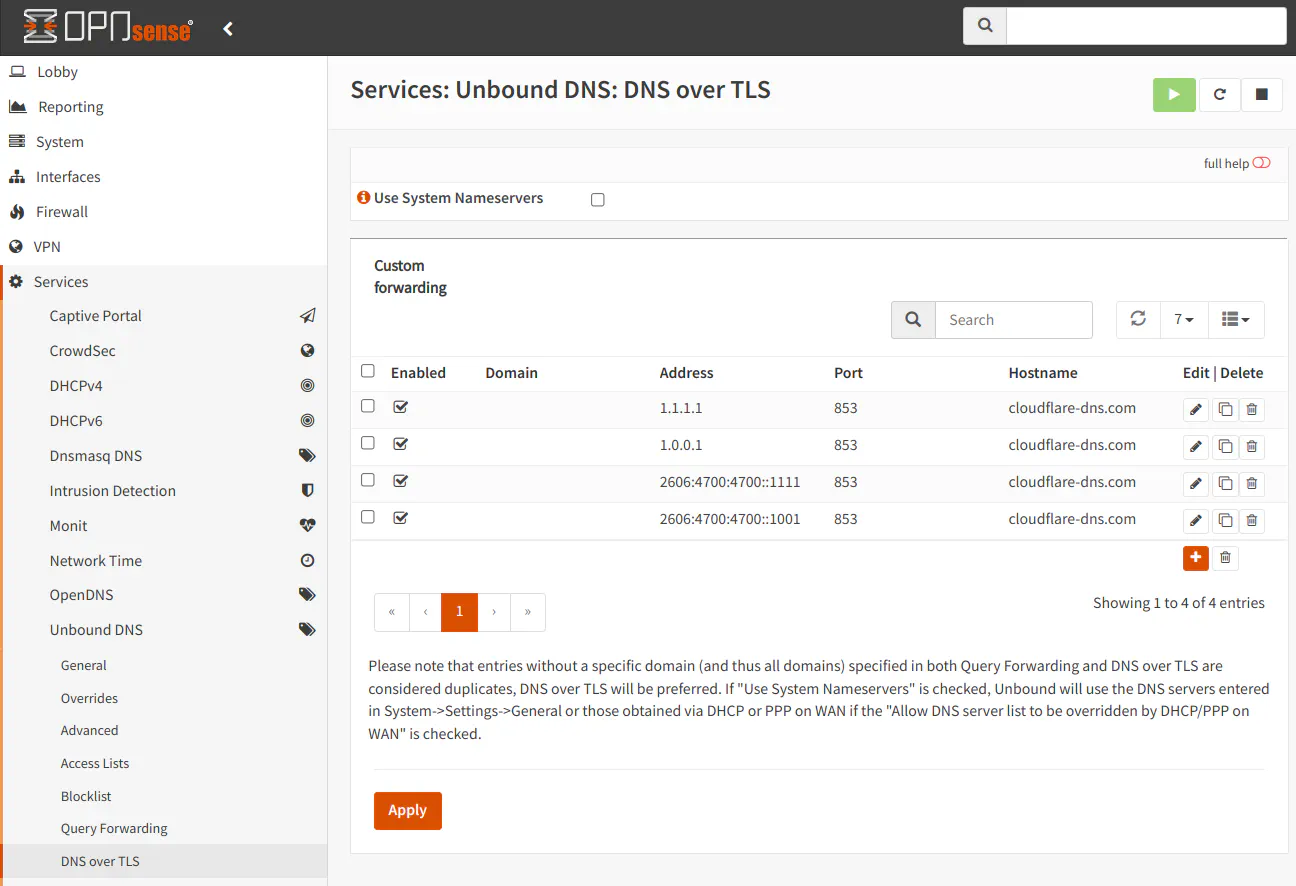
Cloudflare alternatively offers DNS servers which block malware content and malware content plus adult content. To use those servers you simply use different IP addresses. You also need to use a different CN value as well. Use the table below instead of the values in this example if you wish to use the filtered DNS provided by Cloudflare. The port is 853 for all DoT servers so I am not including that value in the table.
| DNS Filter | Server IP | Common Name |
|---|---|---|
| Malware | 1.1.1.2 | security.cloudflare-dns.com |
| Malware | 1.0.0.2 | security.cloudflare-dns.com |
| Malware | 2606:4700:4700::1112 | security.cloudflare-dns.com |
| Malware | 2606:4700:4700::1002 | security.cloudflare-dns.com |
| Malware + Adult | 1.1.1.3 | family.cloudflare-dns.com |
| Malware + Adult | 1.0.0.3 | family.cloudflare-dns.com |
| Malware + Adult | 2606:4700:4700::1113 | family.cloudflare-dns.com |
| Malware + Adult | 2606:4700:4700::1003 | family.cloudflare-dns.com |
System DNS Configuration
In order to use only DNS over TLS for all of your DNS queries for your entire network including the OPNsense system itself, you will need to ensure that you have no DNS servers specified on the “System > Settings > General” page as well as have the “Allow DNS server list to be overridden by DHCP/PPP on WAN” and “Do not use the local DNS service as a nameserver for this system” unchecked.
If you have any of those options set, your OPNsense box and/or your network will use DoT and the DNS servers that are on the list or provided via DHCP on the WAN interface, which is likely what you do not want to happen.
Testing the DoT Configuration
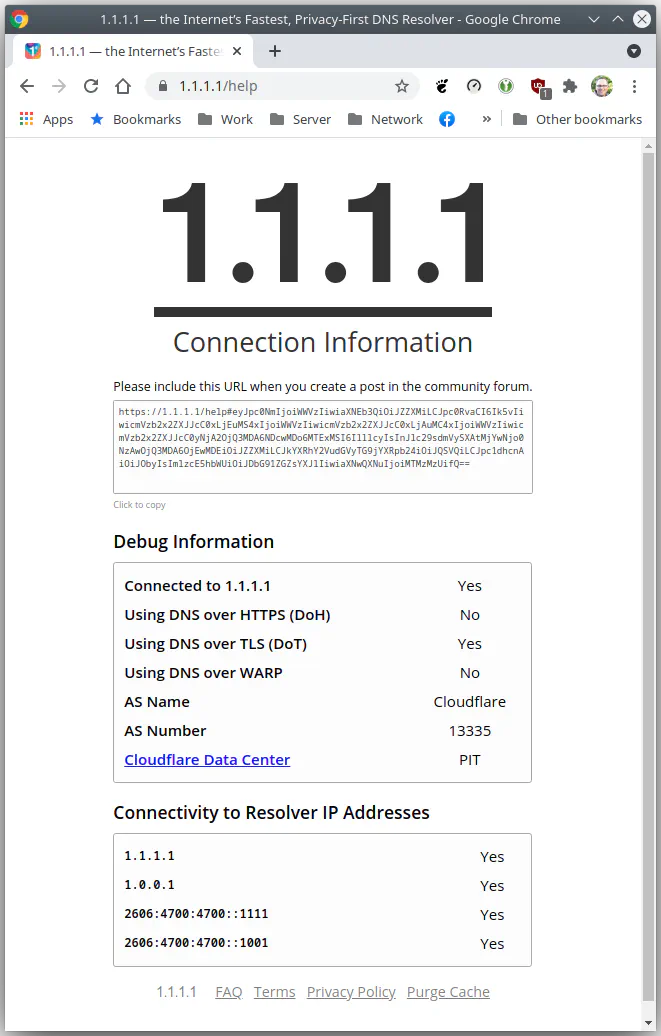
Cloudflare has a webpage on their 1.1.1.1 website in which you can test if DoT or DoH is currently in use if you are using Cloudflare. I noticed that I had to refresh the page after the first check in order for it to show “Yes” for using “1.1.1.1” and show “Yes” for “DoT”. Sometimes it requires me to refresh the page multiple times. I am not sure why I had to do that but once I did that, subsequent refreshes would consistently show “Yes” for “DoT”. Perhaps the test prematurely returns “No” before it is fully complete.
Also, that test page may additionally check if the browser has its own DoT or DoH configuration enabled. For example, my output in both Chrome and Brave browsers only show DoT being used:
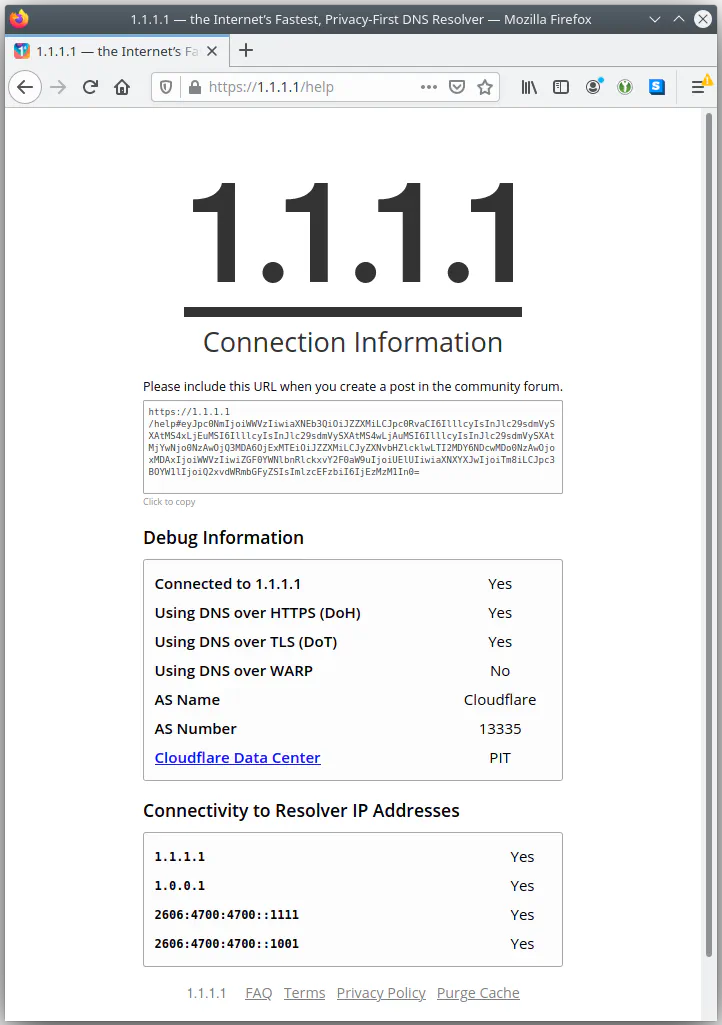
But Firefox shows that DoH is also being used (I cannot recall if Firefox has DoH enabled by default):
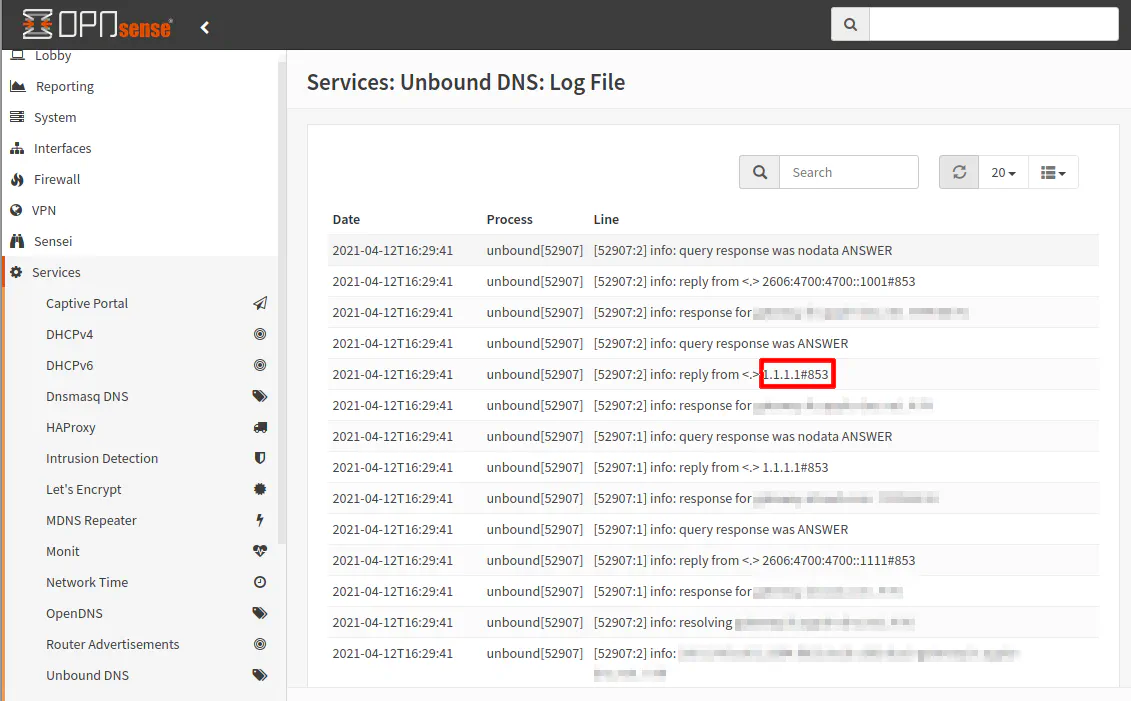
A better way to check if DNS queries are being sent over port 853 would be to go to “Unbound DNS > Advanced” and change the log level to 2 or higher. Be sure that “Log Queries” checkbox is checked as well. Then click “Save”. Be sure to “Apply Changes” at the top of the page in order for the changes to take effect.
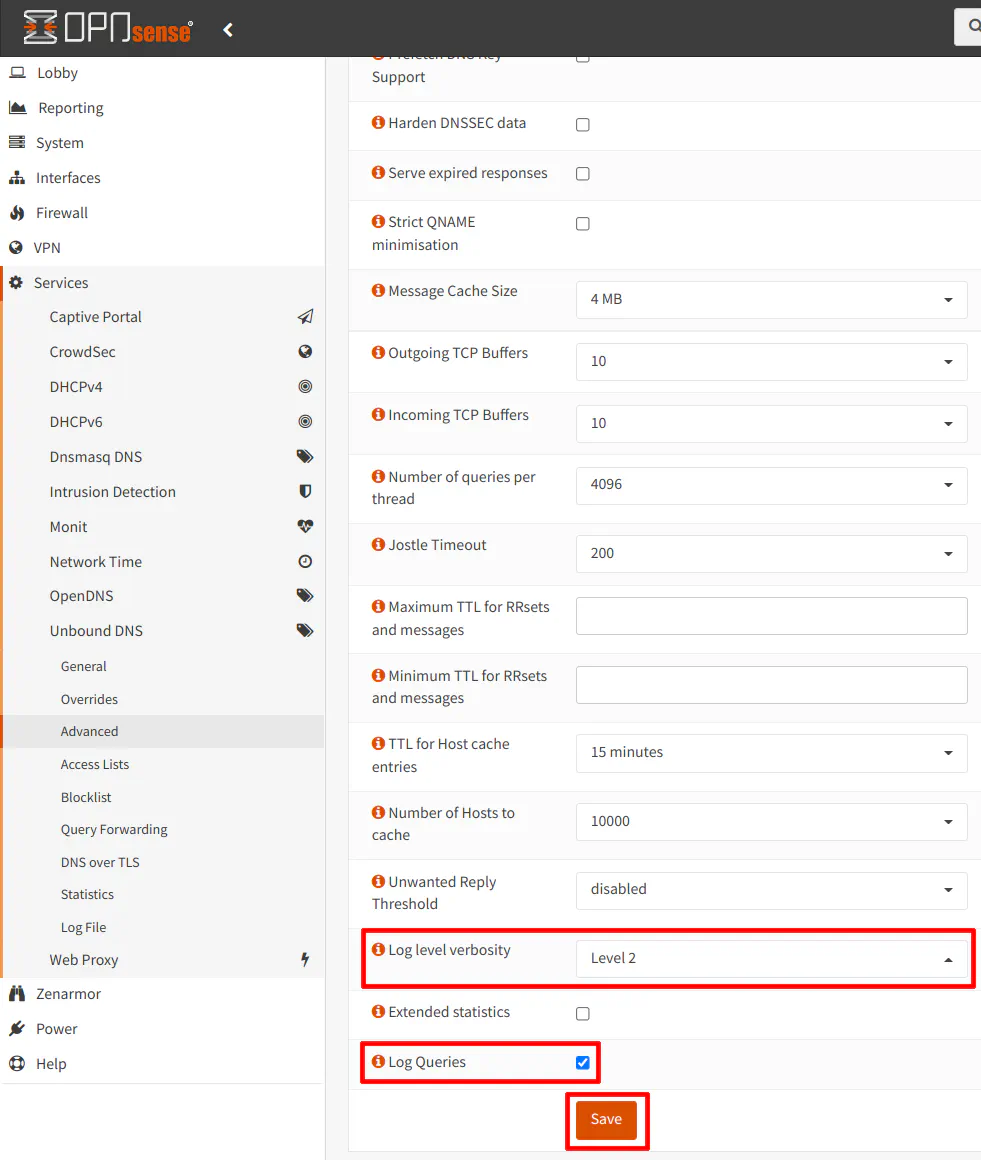
You should see some replies from the Cloudflare DNS servers on port 853:
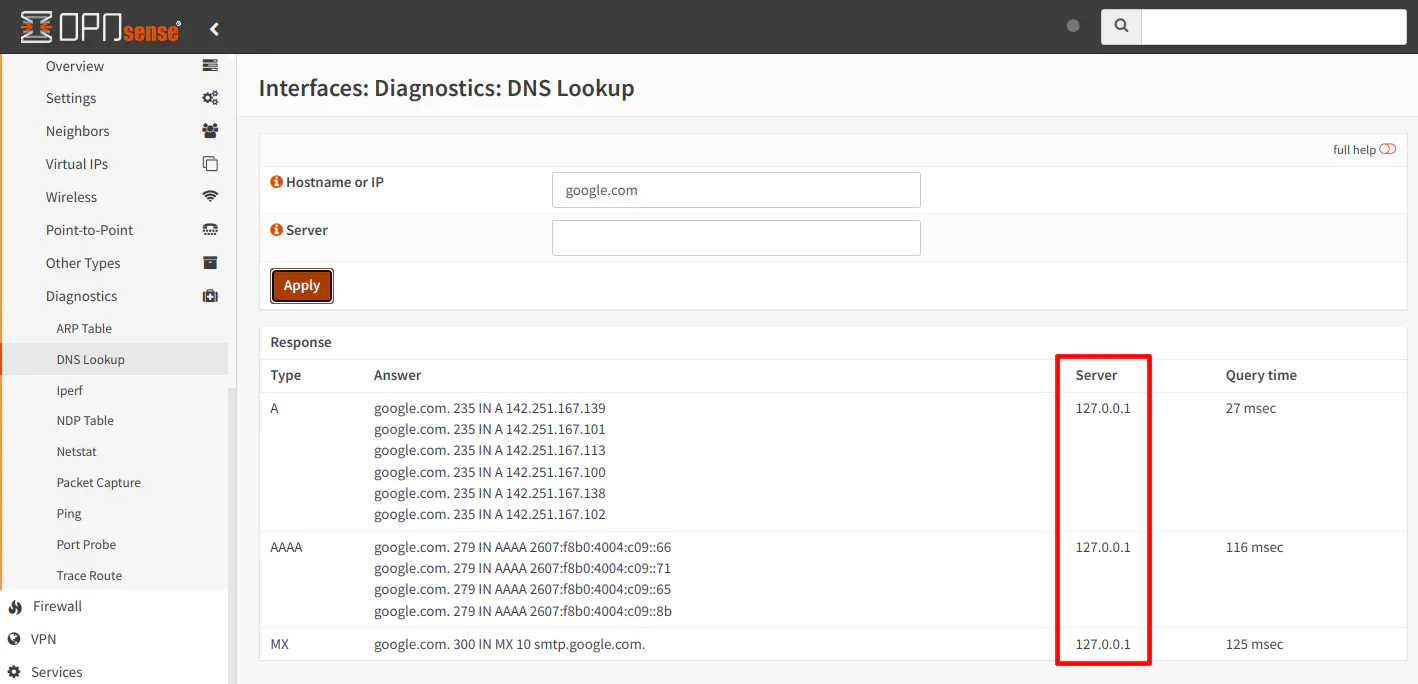
If you wish to see which DNS server(s) OPNsense itself is using, you could perform some DNS lookups by going to the “Interfaces > Diagnostics > DNS Lookup” and viewing which DNS server is being used.
You may only see 127.0.0.1 when using DNS over TLS. This means it is using the local Unbound DNS server for DNS lookups, which should only be using the DNS over TLS servers (assuming proper system DNS configuration mentioned in the previous section). To verify this is true, you can view the Unbound DNS logs as mentioned above after performing a DNS lookup on the “DNS Lookup” page.
Conclusion
That is all you need to do! Native support for DoT makes the process pretty simple. If you want to go further, you can redirect all DNS port 53 requests leaving your network to your Unbound DNS service so that it will be using DoT as well. Also if you want to only use DoT, you could use a public DNS block list to attempt to reduce the amount of DNS over HTTPS traffic as much as possible (in case you have rogue apps/devices which encrypt all DNS traffic over HTTPS to bypass your DNS filters or to provide their own built-in security features).

