Need an Offline Local Network for a Home Lab or IP Video Cameras?
Photo by Mila Naumova from iStock
Table of Contents
Having an offline local network with no Internet access can be useful for a number of reasons. A few that come to mind are home lab networks, non-cloud IoT device networks, and “closed circuit” IP security camera network. For my network, I set up a separate offline IP security camera network using Amcrest IP cameras (affiliate link) as a baby monitor system. The quality is so much better and it is more secure than traditional baby monitors because I can lock down access from outside users.
Configuring the Firewall Rules
Once you have configured the VLAN you plan to isolate, go to “Firewall > Rules > [Your VLAN]”. By default after creating a new VLAN, there are no firewall rules assigned to it. If no rules are added, all outgoing traffic is blocked so the VLAN is already isolated. That was easy!
However, you may want to add a rule to allow DNS traffic to the VLAN interface address if you wish to refer to devices on your isolated network by their hostnames. The Unbound DNS service can still resolve names in your isolated network without allowing any other network traffic through the firewall. This is useful if you prefer using hostnames rather than IP addresses.
I noticed that if you do not create this DNS rule, there tends to be a lot of DNS queries that are blocked by the firewall – at least for my Amcrest IP security cameras. I am assuming the cameras like to phone home to their cloud services even though I have them turned off via the P2P settings to make it easier for novice users to access their cameras from their website or mobile apps. Creating this DNS rule may help keep your firewall logs less spammy since you will not see all of the blocks for DNS requests.
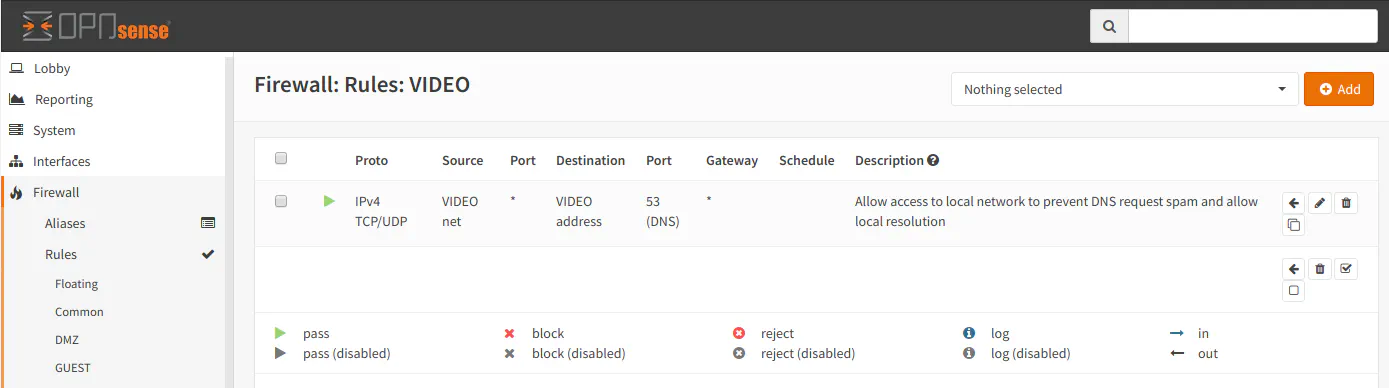
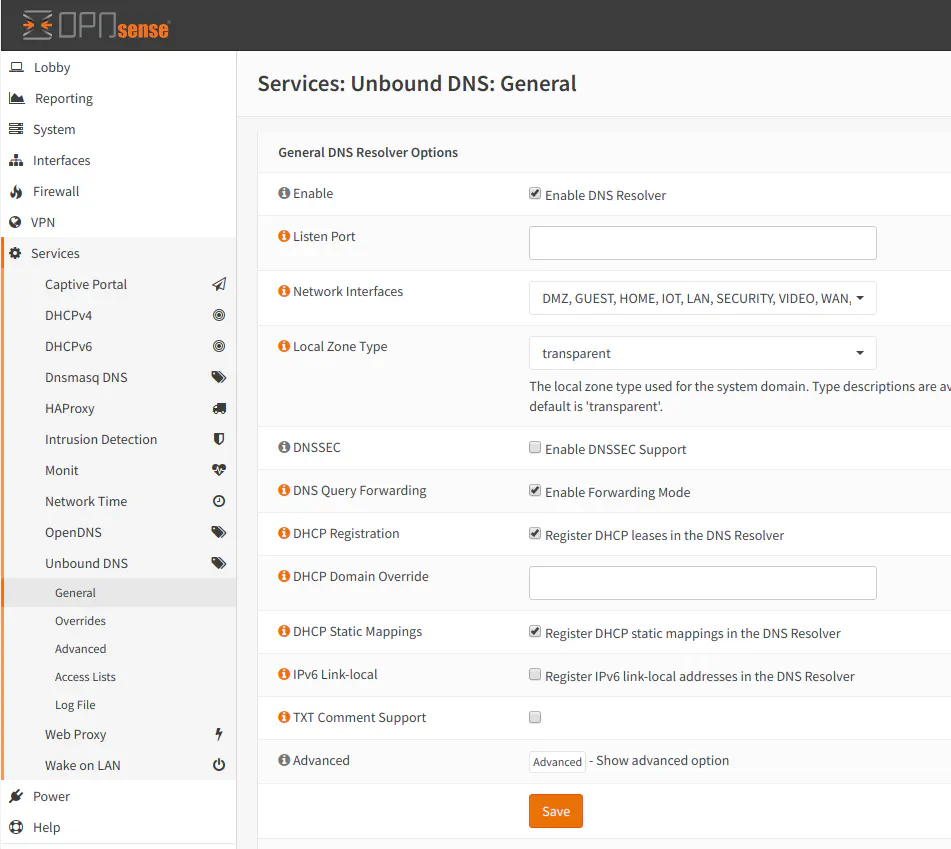
Note: To resolve local device names on your network, you must check the appropriate settings on the “Unbound DNS > DNS” page. Both “DHCP Registration” and “DHCP Static Mappings” settings need checked to allow dynamically and statically assigned devices to register their hostnames with the unbound DNS resolver.
One Important Consideration
Although creating a new VLAN with no firewall rules prevents outgoing traffic and effectively isolates the VLAN traffic from other networks and the Internet, you must be careful not to inadvertently allow incoming traffic from other networks from reaching your isolated VLAN. For instance, the LAN interface that is created when OPNsense is initially installed has a default “allow all” rule which will allow any device in the LAN network to reach any other VLAN in your network.
You should change the “allow all” rule to be more restrictive or you could put a rule above that rule to block access to your other VLAN networks. If you put a rule above to block the other networks, the “allow all” rule will then only allow traffic to go to any external network on the Internet since all of the internal networks have been blocked to keep the networks isolated from one another.
I mention this because it is a potential gotcha for those who are new to writing firewall rules. You may think you have a completely isolated network but may not realize that it is wide open to devices on other networks.

