How to Configure IPv6 in Your Home Network with ISP such as Comcast Xfinity
Table of Contents
IPv6 was drafted in the mid-1990s when it was realized that IPv4 addresses would quickly be exhausted due to the explosive growth of the Internet. Since the IPv4 protocol was originally a research project, approximately 4.3 billion unique IP addresses was considered more than enough. I doubt many imagined our current world where nearly everything would be connected to the Internet.
Various techniques such as assigning smaller sized networks to organizations and the utilization of NAT (Network Address Translation) helped extend the time before IPv4 addresses would be exhausted. IPv4 addresses may finally be exhausted despite the alarm bells sounding in 2011. Despite the early warnings, the world is only at 37.4% adoption according to Google’s stats at the time of the most recent update to this guide.
Conceptually IPv6 is similar to IPv4, but when it came to implementing it, I quickly realized that I left my comfort zone of IPv4. While IPv6 is not necessarily radically different, there are enough differences to make one feel uneasy about the proper way to implement it. I have stumbled my way through the process by reading several articles, blogs, forums, etc., but I am now comfortable enough to have a functioning IPv6 network.
In this how-to, I will be configuring IPv6 in OPNsense using Comcast Xfinity as an example since that is my Internet service provider. If you have another service provider, your configuration may vary especially when it comes to configuring your WAN interface. Also keep in mind that there are other ways you may create your IPv6 network – SLAAC vs DHCPv6, for example.
One thing to be aware of is that I have read that some devices/operating systems do not support or fully support DHCPv6 such as the Android OS. I was not expecting that since I would have thought IPv6 support is well established at this point but it is possible that is not necessarily the case. This information may be out of date, and I do not have any Android phones to test if it is true. You may need to use the “Assisted” option for “Router Advertisements” so that you may use DHCPv6 along with SLAAC for the devices that do not fully support DHCv6 (see the optional section at the end of this how-to).
A word of caution… after assigning IPv6 addresses, you need to ensure you have the appropriate firewall rules in place that (most likely) mimic your current IPv4 rules. There is the possibility that you could break some functionality of your existing network because devices/operating systems often default to use the newer IPv6 protocol once it is enabled and addresses are assigned. I wanted to add this word of caution because it happened to me!
Enabling IPv6 in OPNsense
IPv6 should be enabled by default in OPNsense. I recall turning off IPv6 support when I first set up OPNsense since I did not have time to learn how to properly setup and secure IPv6. I have seen others who have also been hesitant to implement IPv6 until they could fully understand how it works to prevent malicious activity from slipping through via IPv6 or to prevent users from working around firewalls, proxies, etc.
To ensure IPv6 is globally enabled, go to “Firewall > Settings > Advanced”. The first option is “Allow IPv6”.
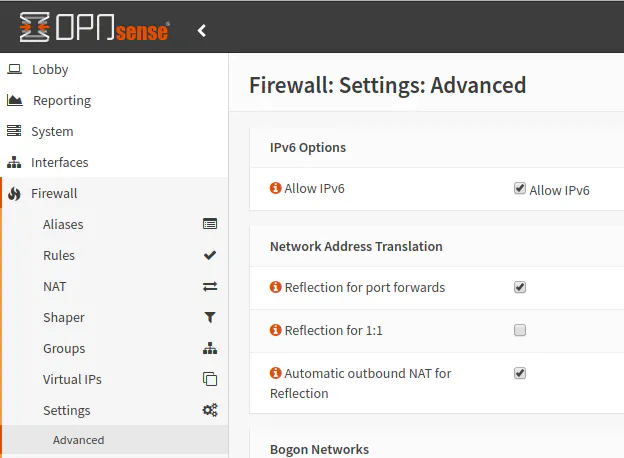
Setting up WAN Interface for IPv6
Now that IPv6 is enabled, the WAN interface needs configured. Go to “Interfaces > [WAN]” to configure the WAN interface. For the “IPv6 Configuration Type”, choose DHCPv6. This allows your OPNsense router to obtain a globally routable IPv6 address from your ISP.
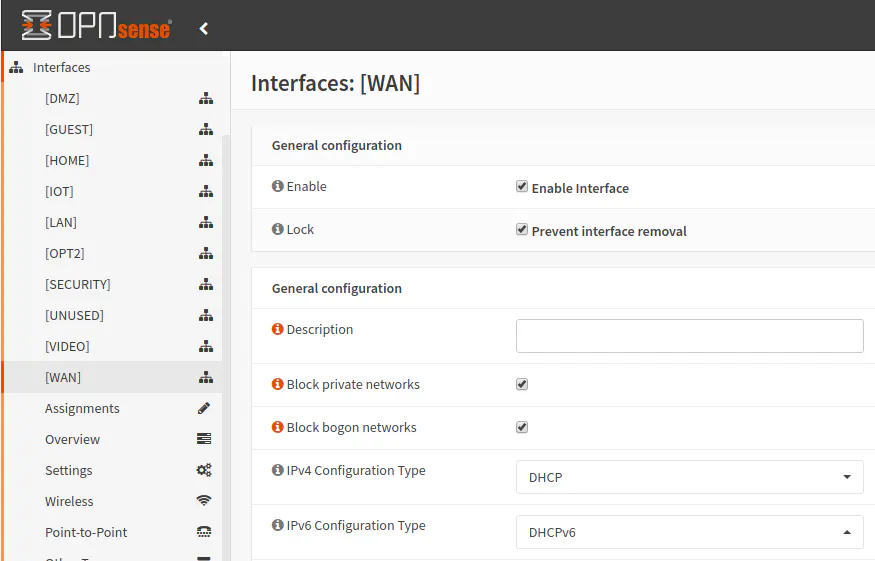
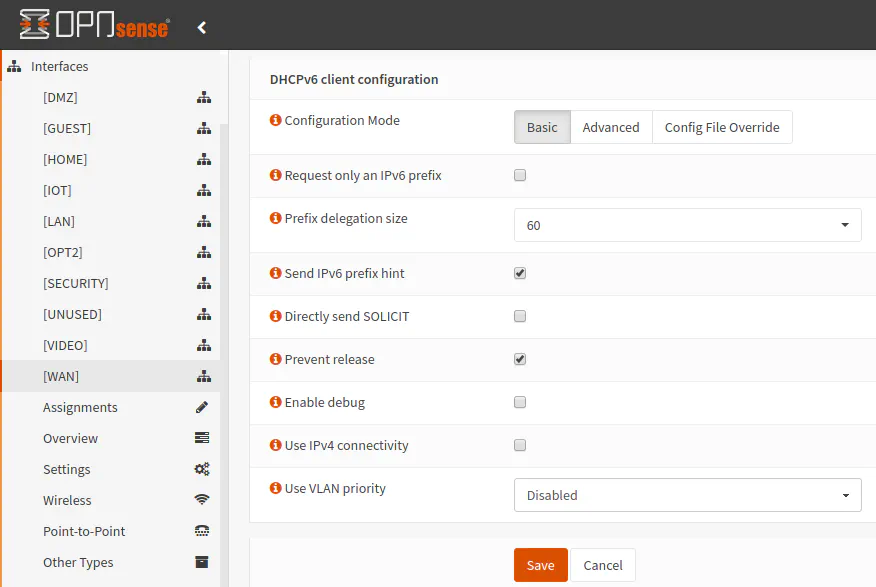
In in the “DHCPv6 Client Configuration” section, a few options will need to be modified. The most important option (if you wish to have more than one VLAN) is to set the “Prefix delegation size” option to “/60”. This will give you a total of 16 networks, which should be plenty for most advanced home networks. If you leave the prefix at the default “/64” size, you can only have one local network. The “/64” prefix is the smallest network allowed by IPv6, which is a huge number of addresses. Because the IPv6 address space is so large, there is no long term concern for exhausting the address space even if everyone has their own “/64” network.
I saw mention that Comcast Xfinity business customers may request a “/56” prefix which would allow for 256 networks, but I do not know if it works for residential customers. Some have said it worked for them while others may have had issues obtaining the address space. I am content with a “/60” prefix since 16 VLAN is more than what I need now and probably in the future (even if I went a little crazy with network segmentation).
You may want to check “Send IPv6 prefix hint” since it sends the desired prefix size to the ISP. I do not know if it is required, but it could help if the ISP requires an implicit request.
One other thing is that you may want to check “Prevent release” to attempt to hold onto your assigned IPv6 address so that they will not change as often. Most likely, your IPv6 addresses will only change if you have been disconnected from the Internet for a while and your DHCP addresses are released. Of course, this may vary from one ISP to another.
The “Prevent release” option may only be important to you if you are hosting a public server and are referring to your IPv6 address directly. Like with IPv4, you could periodically run a script to update your IPv6 (AAAA) DNS record to keep your IPv6 address up to date if it happens to change, which would make the need to prevent your IP address from changing even less of an issue.
Verifying WAN IPv6 Address
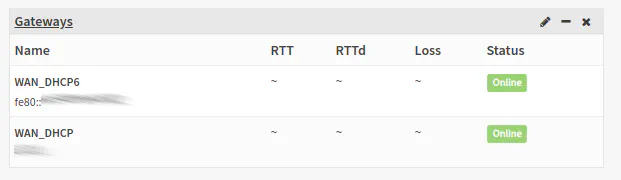
With your WAN interface configured properly, you may notice on your OPNsense dashboard that you will have two gateways – one for IPv4 and one for IPv6. This is something that occurs automatically. You do not need to configure a second gateway for IPv6 manually. I tried that at one point when I was learning how to configure IPv6, but I realized that it was not necessary.
One thing that confused me and had me thinking that I did not have IPv6 configured properly is that the dashboard shows the link local IPv6 address and not your globally routable IPv6 address. A link local address will usually begin with “fe80”.
If you want to see your globally routable IPv6 address assigned to your router by your ISP, go to the “Interfaces > Overview” page. Once there, scroll down to the WAN interface and click the arrow to expand the WAN interface to reveal its detailed information.
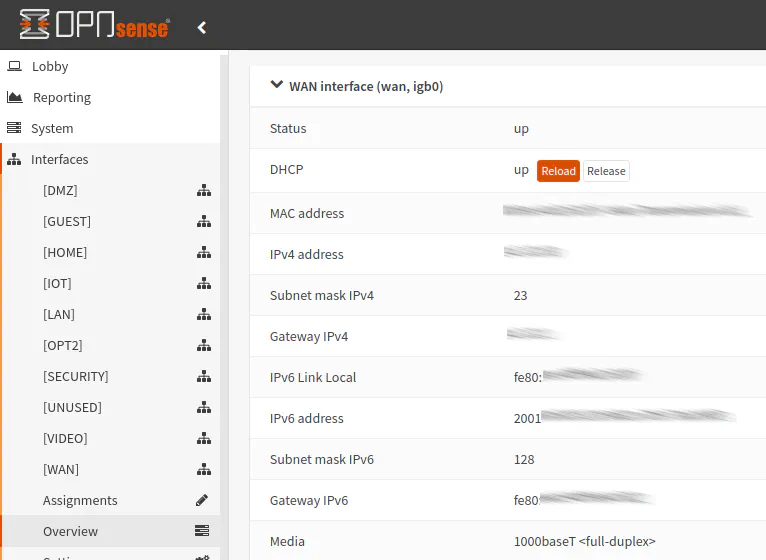
You will see the same IPv6 link local address as displayed on the OPNsense dashboard but below it you should see your global IPv6 address. It may begin with “2001” or “2601”. Those seem to be common addresses assigned to routers by Comcast (and possibly other ISPs) based on various discussions/posts I have seen in my research. If you can see such, it is a promising sign that you are properly set up on the WAN interface.
We can go a step further in verifying IPv6 is working on the WAN interface by pinging a website from the WAN IPv6 address. Go to “Interfaces > Diagnostics > Ping”. For the “Host” enter “google.com” or any website that is accessible via IPv6. Select “IPv6” as the IP protocol. The “Source Address” can be left at the default, which should be the WAN interface. You can select WAN if you want to be certain it is using that interface. The default “Count” of 3 is adequate for testing IPv6 connectivity.
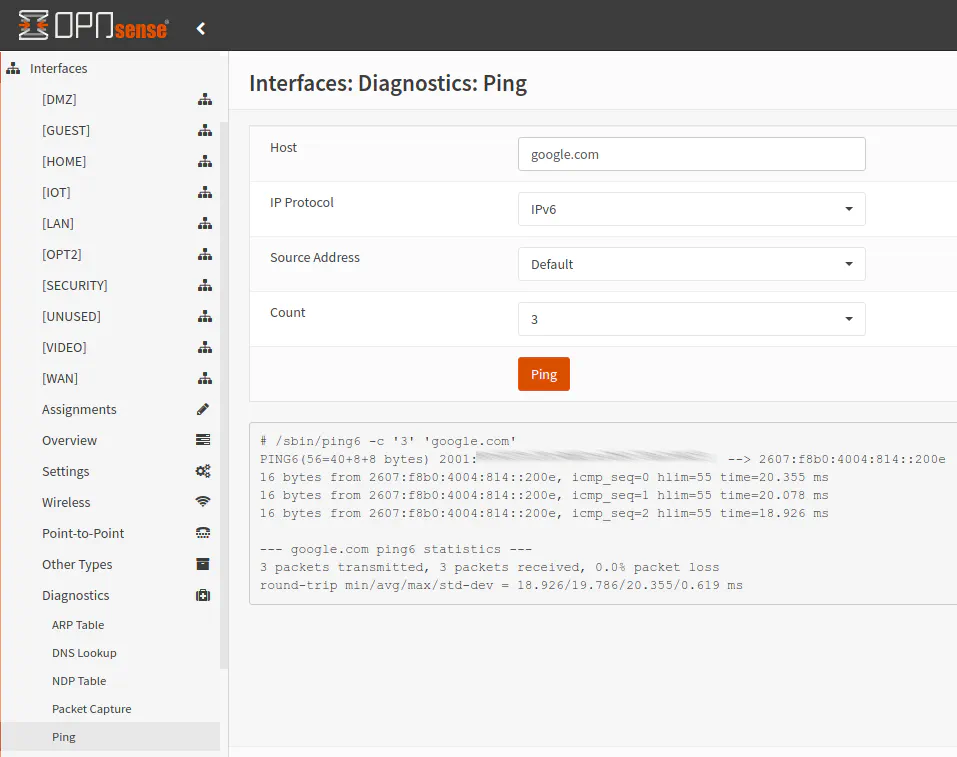
You should notice that your IPv6 WAN address is the source address (which mine begins with “2001”) and the destination address is google.com’s IPv6 address, which begins with “2607”. If you received all of the packets, you should have the WAN setup properly. Congrats!
Now we need to move on to the LAN network(s) to fully enable IPv6 in your network.
Allowing ICMPv6 Traffic on WAN Interface
ICMP is more important for IPv6 than it is for IPv4. Therefore, you should allow certain types of ICMPv6 traffic for proper IPv6 communication. When researching this topic, I came across some recommendations for the ICMPv6 traffic that should never be blocked according to RFC 4890. These are the following:
- Destination Unreachable (Type 1) - All codes
- Packet Too Big (Type 2)
- Time Exceeded (Type 3) - Code 0 only
- Parameter Problem (Type 4) - Codes 1 and 2 only
- Echo Request (Type 128)
- Echo Response (Type 129)
On the “Firewall > Rules > WAN” page, you can enter each of the following rules above (except “Packet Too Big”) by following the example rule configuration:
| Option | Value |
|---|---|
| Action | Pass |
| Interface | WAN |
| TCP/IP Version | IPv6 |
| Protocol | ICMP |
| ICMP type | Destination Unreachable |
| Source | any |
| Source Port | any |
| Destination | WAN address |
| Description | Allow ICMPv6 destination unreachable |
Create a rule for each type of ICMP traffic by cloning the rule and changing the “ICMP type”.
Configuring LAN interface(s)
Configuring the LAN/VLAN interfaces took me longer to figure out because there are several options you can select for assigning IPv6 addresses to your devices: Static IPv6, DHCPv6, SLAAC, 6rd Tunnel, 6to4 Tunnel, and Track Interface. Whew! Which option to choose? There are more options to choose from than IPv4 (if you do not count all of the IPv4 point to point connection options). With IPv4, one would choose either static or DHCP to configure IP addresses.
Some have suggested using “SLAAC” while others have suggested using “Track Interface” which works with DHCPv6 (the IPv6 version of DHCP). SLAAC dynamically generates IPv6 addresses based on an algorithm. Originally, SLAAC included the unique MAC address of the network device but in our secure-aware/tracking-aware world, it was realized that generating deterministic IPv6 addresses would be problematic from a privacy/security perspective.
Since I am requesting multiple prefixes from my ISP using DHCPv6 on the WAN interface, I decided to use DHCPv6 for assigning addresses to my VLAN interfaces and network devices. I do not know how SLAAC works when requesting multiple prefixes for your network. However, SLAAC may be the easiest option if you only have one LAN interface since it requires less configuration. DHCPv6 is likely to be the choice many advanced home network users will pick due to being able to obtain a larger network prefix for network segmentation.
Keep in mind that a prefix size of “/60” is considered to be a larger prefix size than “/64” because it allows the last 4 bits of the first 64 bits of an IPv6 address to be assigned to various subnetworks/VLANs. A “/64” prefix indicates a single IPv6 network. This is similar to IPv4 when using the CIDR notation ("/8" is a larger network than “/24”, for instance).
To configure the LAN interface(s), go to “Interfaces > [LAN]” (or another VLAN). For “IPv6 Configuration Type”, select “Track Interface”. That should cause the “Track IPv6 Interface” section to display on the current page.
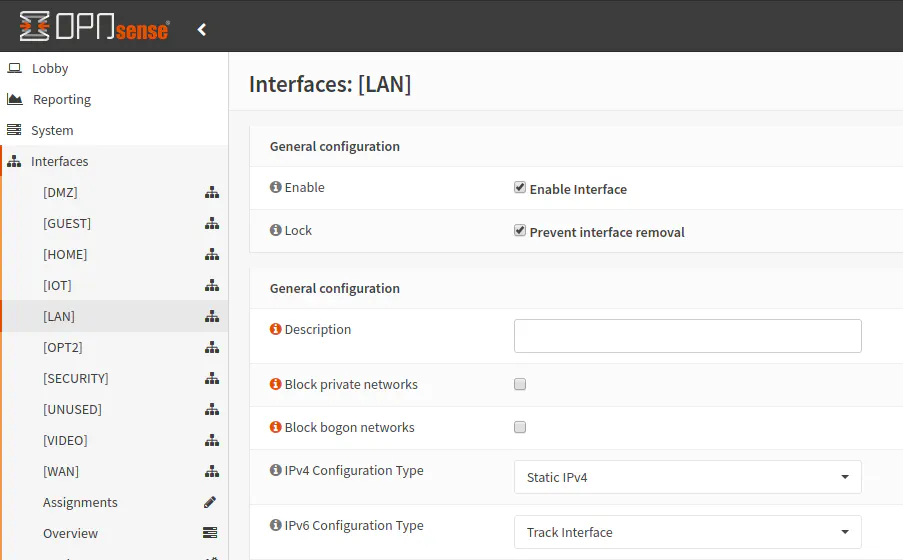
The “IPv6 Interface” to track should be set to WAN unless perhaps you have more than one WAN interface/gateway. For the “IPv6 Prefix ID”, you may enter anything from 0 to F (hexadecimal) since we have 4 bits to allocate to our local networks (up to 16 networks). So that means we can enter 0-9 for the first 10 networks and then A-F for networks 11 through 16. For my network, I just started with 1 to be similar to IPv4 (192.168.1.0). Also, I was not sure initially if the WAN interface would use the 0 (zero) prefix ID. Then I realized that my WAN interface is assigned its own IPv6 address starting with “2001” by Comcast and my VLANs got assigned to another completely different network starting with “2601”. I was not expecting that, but I think it may be a common practice by ISPs (or at least Comcast). (Perhaps viewers of this site could shed some light on why this is the case in the comments section on this page.)
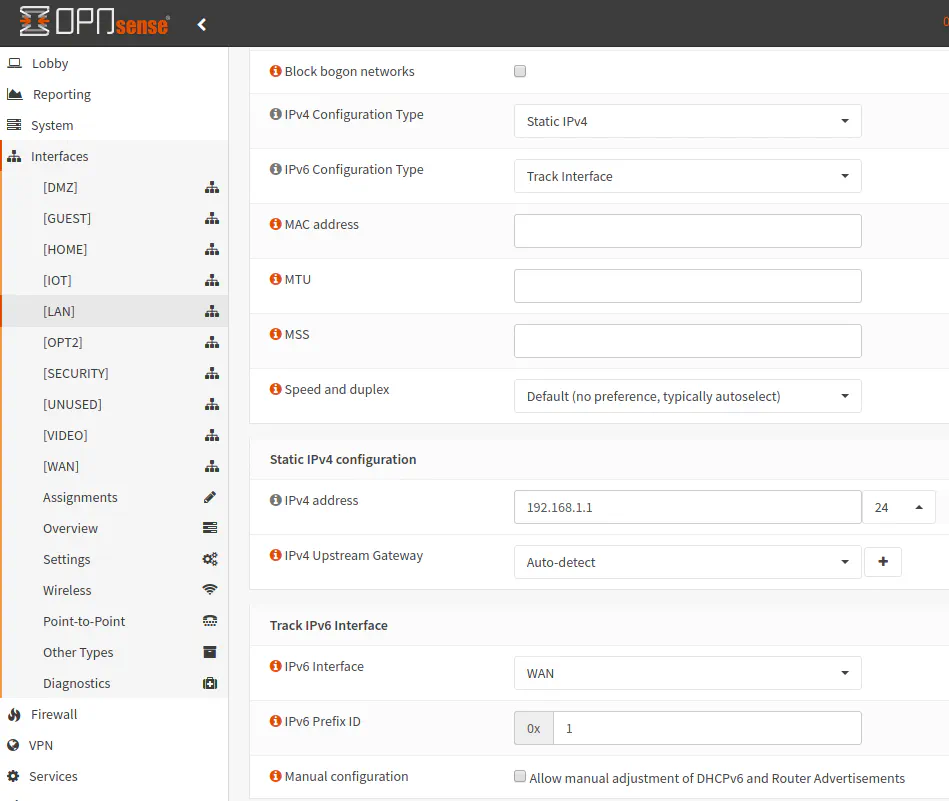
That should be all you need to do to for the interface configuration. Repeat this process for all of your networks. You may not reuse any of the prefix IDs. You need to use 0-9 and A-F if you have a “/60” prefix.
A Basic Set of IPv6 Firewall Rules for LAN/VLAN Interfaces
Creating firewall rules for IPv6 is not greatly different than IPv4 rules. In fact, some IPv4 and IPv6 rules may be combined into a single rule since OPNsense allows you to select both protocols when adding/editing rules. This functionality is useful when you are allowing or blocking ports on a particular interface or defining rules which are not specific to either protocol.
If you are only using the default LAN network that was created when you installed OPNsense, you may want to simply leave the default “allow all” rule unless you wish to be more restrictive by only allowing outgoing HTTP/HTTPS, etc. However, you really need to understand all of the traffic on your network before you start locking down outgoing traffic. Otherwise, you could break various services which use non-HTTP/HTTPS ports. The rules I am discussing below will be much more beneficial when you have more than one network configured in OPNsense (either separate physical networks or VLANs).
As of OPNsense 19.7, the ability to see what firewall rules are autogenerated for IPv4 and IPv6 protocols was added. Autogenerated rules cannot be modified since they are essential rules for proper functioning of the firewall. The autogenerated rules can be viewed by clicking on the icon with a down arrow and rule count indicator on the first row of the rules page. You will notice on the LAN interface under the Firewall rules page that there are several IPv6 rules to allow access to the DHCPv6 server on the LAN network using the link local addresses. These rules are essential for IPv6 to function properly, which is why they cannot be disabled (at least not easily from the web interface).
Below is a screenshot showing the autogenerated rules for the LAN interface:
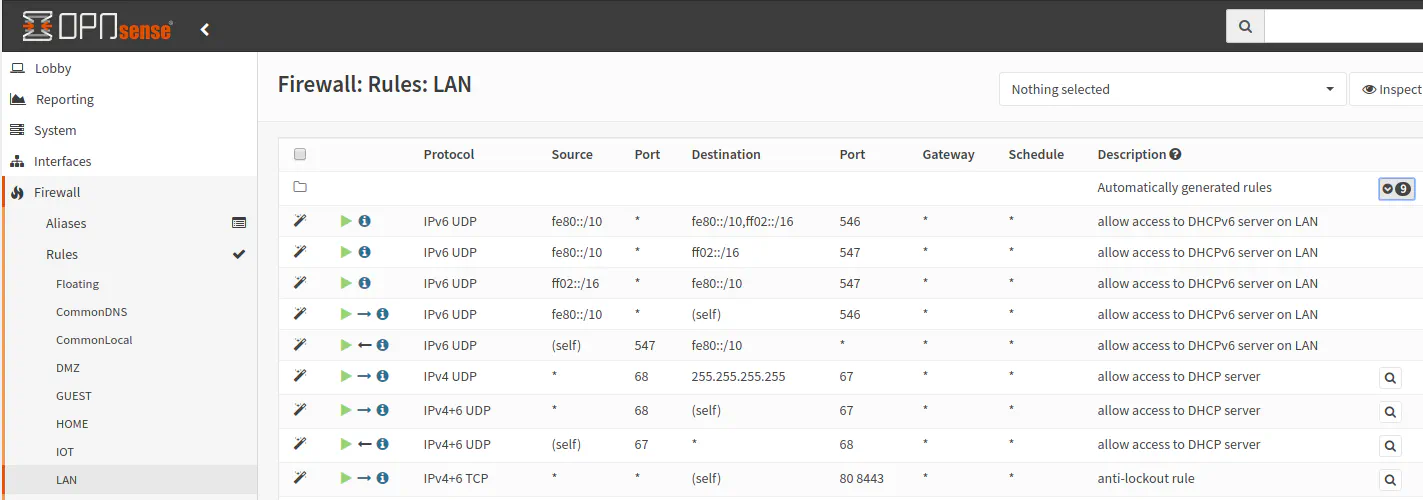
At a bare minimum, you may want the following two rules:
- A rule to allow access to the network interface’s DNS server
- A rule to block access to other VLANs on your network but allows Internet access
As I discussed in my OPNsense firewall rules how-to, rules are evaluated from top to bottom of the rule list. Once the traffic matches a particular rule, no other rules are evaluated. Therefore, you need to put your most specific/strict rules first followed by the more general rules. Unless you are locking everything down super tight, the last rule most likely will be an “allow all other traffic” rule. For home use, that may be sufficient since that makes your firewall act more like a consumer grade router and traffic will flow as most home users would expect.
I am going to use the LAN network as an example, and I am assuming you are using the rules below instead of the default “allow all” rule. You can repeat these bare minimum set of rules on all of your other interfaces. Be sure to substitute “LAN net” and “LAN address” for the appropriate interface.
Allow Access to the Network Interface’s DNS server
The first rule you want in your list is a rule to allow access to the DNS server on the network’s interface. By default Unbound DNS listens on all network interface IP addresses. If you do not create this rule, the second rule will end up blocking access to the DNS server since the IP address is a private network address.
To create the rule to access the network interface’s DNS server, you can simply use the built-in aliases in OPNsense. The built-in aliases are useful because it allows you to combine both IPv4 and IPv6 into a single rule. The “LAN net” alias refers to the entire LAN IP address range which you have defined when creating your interfaces. By default it would be 192.168.1.0-192.168.1.255. The “LAN address” alias refers to the interface address of 192.168.1.1:
| Option | Value |
|---|---|
| Action | Pass |
| Interface | LAN |
| TCP/IP Version | IPv4+IPv6 |
| Protocol | TCP/UDP |
| Source | LAN net |
| Source Port | any |
| Destination | LAN address |
| Destination Port | DNS (53) |
| Description | Allow access to the LAN DNS server |
Block Access to Other VLANs but Allow Access to Internet
This second rule should always be the last rule in your ruleset. If you wish to allow other specific access to devices/networks, you should put the rules above this second rule. The rule below blocks access to all private network addresses and allows access to any other network that is not a private network which means all IP addresses on the Internet. You may read the following rule as: “allow access to any network that is not a local network”. When I first started writing firewall rules, I achieved this concept using two separate rules but then I learned from other examples that I saw that I can use the “Destination / Invert” option to combine two rules into a single rule.
You will need to enter the IPv6 range allocated by your ISP along with the IPv4 private IP addresses in the “PrivateNetworks” alias. In the example below, substitute 2601...::/60 with your own IPv6 range. You will want to end the address range with ::/60 if you are using “/60” as your IPv6 prefix delegation so you only need to enter the first half. If your IPv6 address changes, you will unfortunately need to update the “PrivateNetworks” alias. OPNsense has introduced dynamic IPv6 host aliases in 22.1 but they are used for individual hosts on your network. You should make use of those types of aliases for allowing specific access to IPv6 services.
| Option | Value |
|---|---|
| Action | Pass |
| Interface | LAN |
| TCP/IP Version | IPv4+IPv6 |
| Protocol | any |
| Source | LAN net |
| Source Port | any |
| Destination / Invert | checked |
| Destination | PrivateNetworks (alias containing: 10.0.0.0/8,172.16.0.0/12,192.168.0.0/16,2601…::/60) |
| Destination Port | any |
| Description | Allow access to Internet and block access to all local networks |
Technically the IPv6 range specified in the “PrivateNetworks” alias are public IPv6 addresses, but we are treating those networks as private networks since those networks reside behind our firewall for local networks. We are using the firewall rule above to restrict the network traffic between our local networks. Remember, even though the IPv6 addresses are publicly routable on the Internet they are not publicly accessible by default.
(Optional) Create Statically Assigned IPv6 Addresses via DHCPv6
While the above will be sufficient to have a basic functioning IPv6 network, you may desire to assign static IPv6 addresses to your devices via your router similar to IPv4. This is a convenient way to centrally assign static addresses without the need to go to every device and enter the static IP configuration. There are extra steps you must take to statically assign IPv6 addresses if you are using DHCPv6.
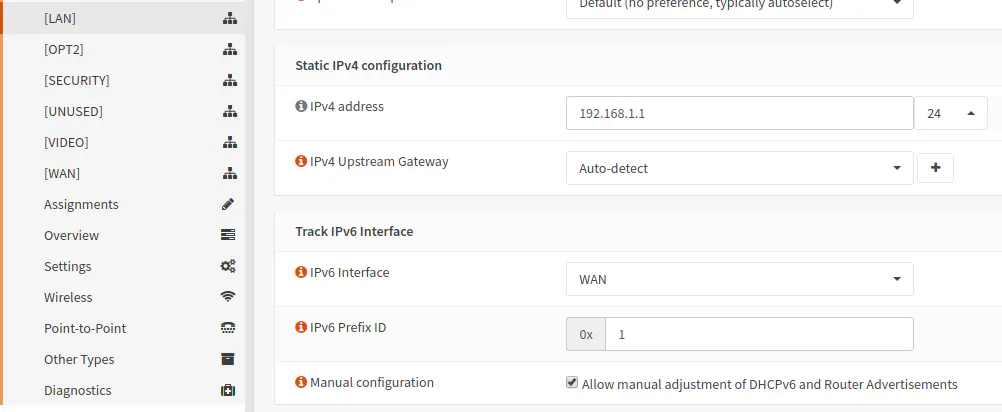
Allow Manual Adjustments for DHCPv6 and Router Advertisements
Go back to each interface’s page like I mentioned in the “Configuring LAN Interface(s)” section. In the “Track IPv6 Interface” section, check “Allow manual adjustment of DHCPv6 and Router Advertisements”. This option enables the LAN interface, for instance, to show up on the DHCPv6 services page.
Enable DHCPv6 Server to Apply Manual Adjustments
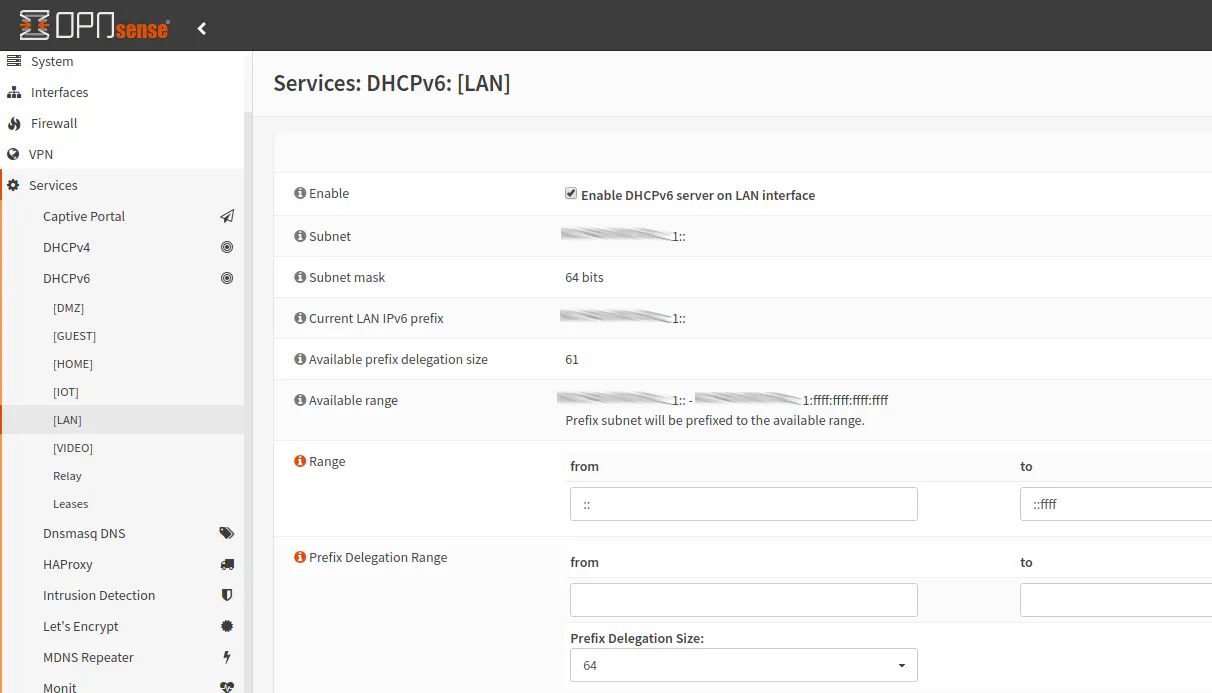
Since we are manually configuring DHCPv6, you will need to enable the DHCPv6 server to allow manual changes to take place. This step is sort of confusing because we already set up the DHCPv6 service when enabling “Track Interface” for all of our interfaces and IPv6 address do get automatically assigned. However, when you want full control so you can specify the DHCP range and statically assign IPv6 addresses (among other options), it seems the manual changes have to be enabled in this manner.
Now to go “Services > DHCPv6 > [LAN]”. Check “Enable DHCPv6 server on LAN interface” and then enter your desired DHCPv6 range. This range is what is automatically assigned to any of your network devices that are set to automatically obtain an IPv6 address through DHCP. It is not the range that you use to statically assign IPv6 addresses. Any static IPv6 address must fall outside of the specified range. To keep things relatively simple, you may just use the last 2 bytes/16 bits of the IP address since that still provides you a whopping 65,536 addresses! You will notice that the second half of the IPv6 address is displayed on the page and the full range of addresses is possible to select from:
:: - ::ffff:ffff:ffff:ffff
The double colon means there are consecutive sets of zeros such as 0000:0000:0000:0000. So the above range could be written as 0000:0000:0000:0000 - ffff:ffff:ffff:ffff. This syntax is a shorter way to write IPv6 addresses since they are much longer than IPv4 addresses. Because the first half of the IPv6 address (the delegated prefix/subnet) has already been assigned, the DHCPv6 settings are only concerned with the second half of the address, which is why there is nothing displayed before the double colon. For our example, if you want to use the last 2 bytes/16 bits of the IPv6 address for DHCP simply enter the range:
:: - ::ffff
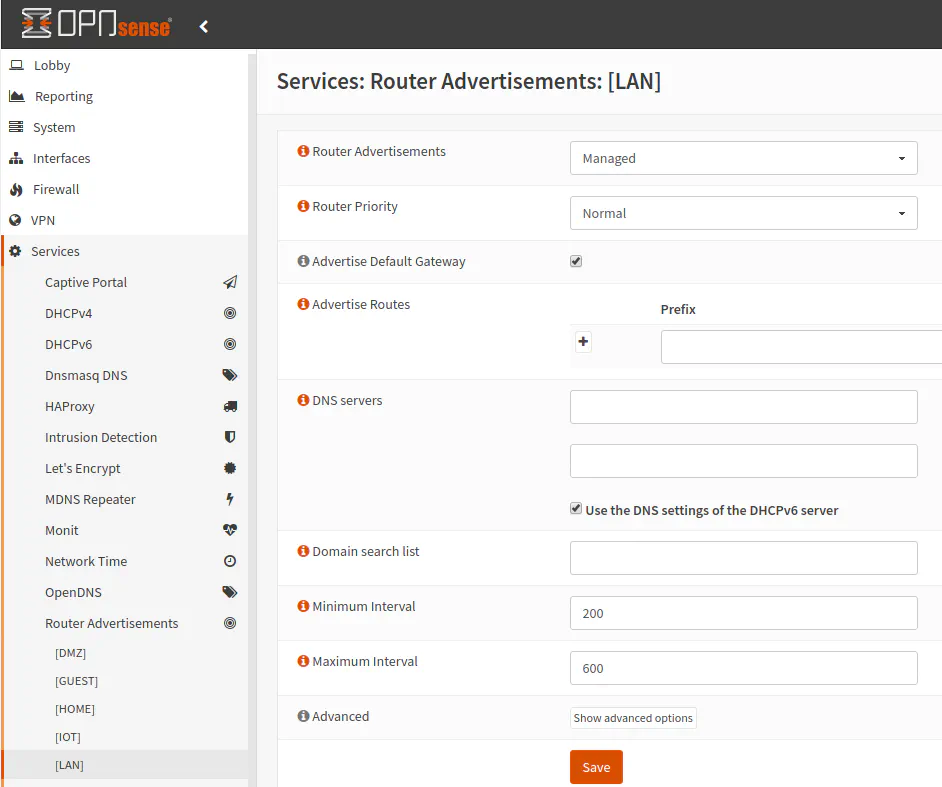
Configure the Router Advertisements for Each Interface
To adjust the “Router Advertisements” which works alongside DHCPv6, go to “Services > Router Advertisements > [LAN]”. Set the “Router Advertisements” to “Managed” if all of your devices support DHCPv6 or to “Assisted” if you have any devices which may not fully support DHCPv6. I believe this allows assigning IPv6 address with SLAAC. As mentioned earlier in this how-to, Android devices may not fully support DHCPv6. Again, I have not verified if that is true.
The only other option you may want to adjust is checking the “Use the DNS settings of the DHCPv6 server” option. I am not sure how necessary it is, but I checked it just in case because I am not manually specifying any special DNS servers for this specific interface on the “Router Advertisements” page. I would assume that leaving the DNS fields blank that it would default to the DNS servers that are specified by the DHCPv6 server (similar to the IPv4 configuration), but that may not be the case for IPv6.
Statically Assigning IPv6 Address
Finally after all that prior configuration, you can now start assigning IPv6 addresses. The interesting thing about creating a static IPv6 address is that you need to know the DUID of each device rather than using the MAC address like with IPv4 (but some MAC addresses may be visible in the “DUID/MAC” column of the “Leases” page). The DUID is something that is generated by the operating system of each device so even if you swap hardware, the DUID stays the same until you reinstall the operating system. I could not figure out how to find the DUID in Linux or even if you can discover what it is on devices like an iPhone. However, you can sometimes see the manufacturer in the “DUID/MAC” column which can help you identify the device.
The “Services > DHCPv6 > Leases” page lists all of the devices which have been assigned an IPv6 address via DHCPv6. If a device is not showing up, you may need to reboot the device (or possibly your router). I have personally noticed that not every device that has an IPv4 address shows up properly on the “DHCPv6 Leases” page, and I believe I have seen others have issues with that as well. Perhaps not all devices play friendly with IPv6 or OPNsense needs to provide additional IPv6 support to resolve such issues. Perhaps some devices are using SLAAC instead of DHCPv6 to obtain an IPv6 address and therefore would not show up in the DHCPv6 leases page. When in doubt, you may list out the IPv6 addresses on the device itself with a simple command to help you identify devices on the “Leases” page.
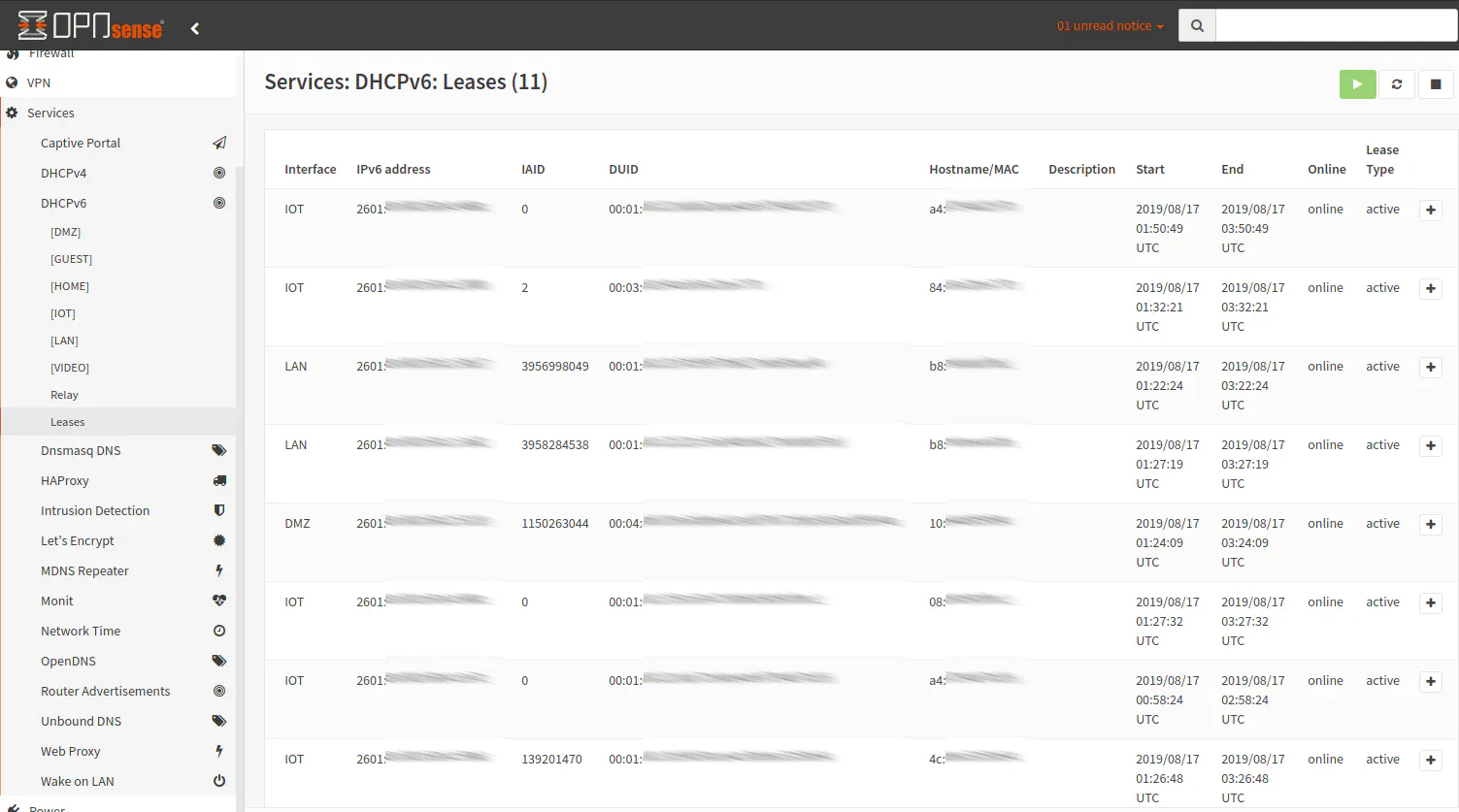
From the “Leases” page, you can click the “+” button to set up a static IPv6 address. The DUID will automatically be filled in for you which is nice because it is a long identifier to need to type. You need to make sure you pick an IPv6 address outside of the range of the DHCP address range that you specified earlier. When entering an IPv6 address, you may enter the full IPv6 address or just the second half of the IPv6 address if you have dynamic IPv6 addresses. If you enter only the second half, you must start the address with :: (2 colons).
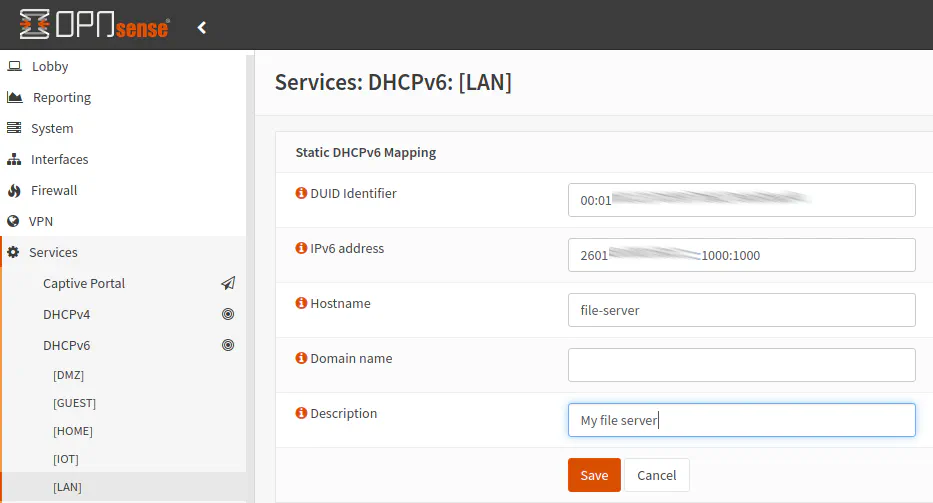
If you wish for the static DHCPv6 lease to take effect immediately, you may try disconnecting the device from the network and reconnecting it by clicking on your network icon on your taskbar, toggling the WiFi disable/enable button, etc. depending on the type of device you are using. You may also issue a DHCP release and renew command as well (such as in Linux, for example).
Testing IPv6
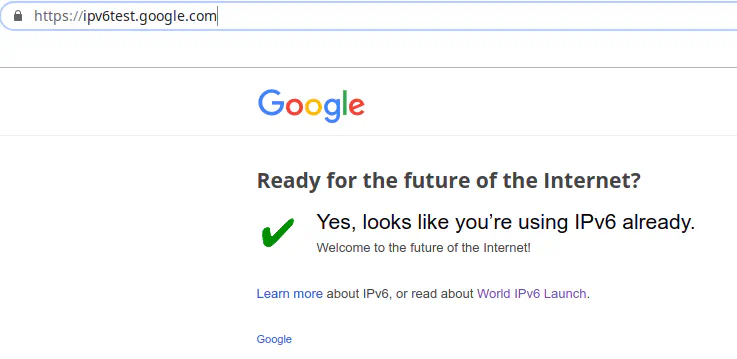
You may want to test IPv6 connectivity on the Internet by accessing a site such as Google’s IPv6 test site to see if you can access it via IPv6:
Or you may try a more detailed test as shown in the screenshot below:
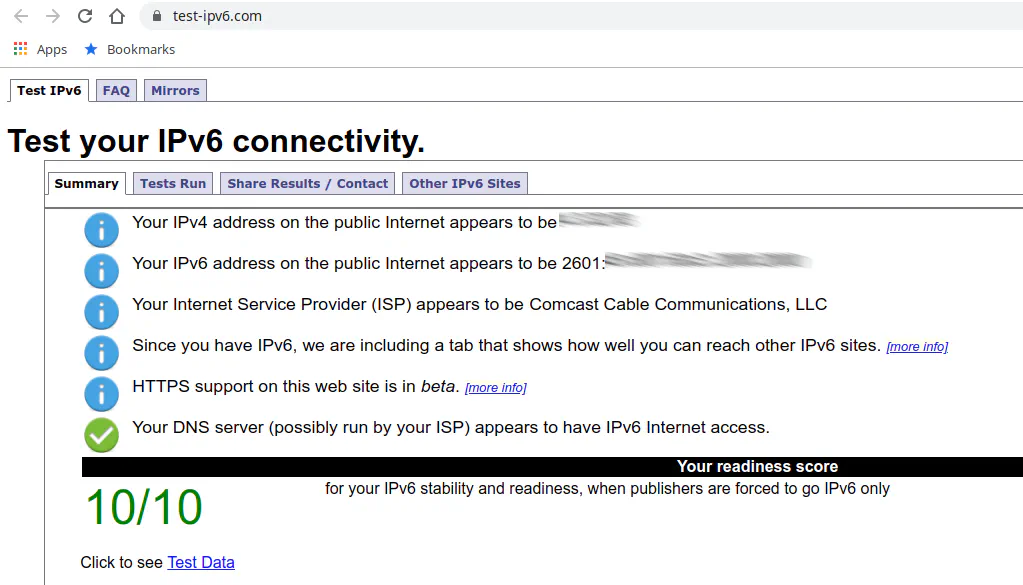
There you have it! A basic but detailed explanation of what I learned when enabling IPv6 on my network. Please keep in mind that there are likely other ways to configure IPv6 depending on your ISP. This guide discussed the approach that seemed to work well for me based on the ISP that I am currently using. I have not experimented much with IPv6 beyond the basic functionality. It took me a little while to begin to understand how to properly configure IPv6 – more time than I thought it would take to be honest. Since I am still learning, please feel free to provide constructive feedback so that I can improve the information contained in this guide.

